Getting Started
You may have heard people say that “getting started with Little Snitch may be tough” because there are so many connection alerts. And indeed: If you start with an empty rule set and choose alert mode, Little Snitch has to ask about every network connection an app or the operating system performs — and that’s a lot.
We at Objective Development are well aware of this, so we provide tools to help you get started:
- There is Silent mode, which collects individual data before you decide what to allow or deny.
- There are groups of pre-configured rules which allow things by topic (e.g. everything from Apple).
- You can add ready-made blocklists, which block things by topic (e.g. trackers, ads, malware).
As a first-time user, Little Snitch asks you whether to enable pre-configured rule groups and whether to use silent mode:
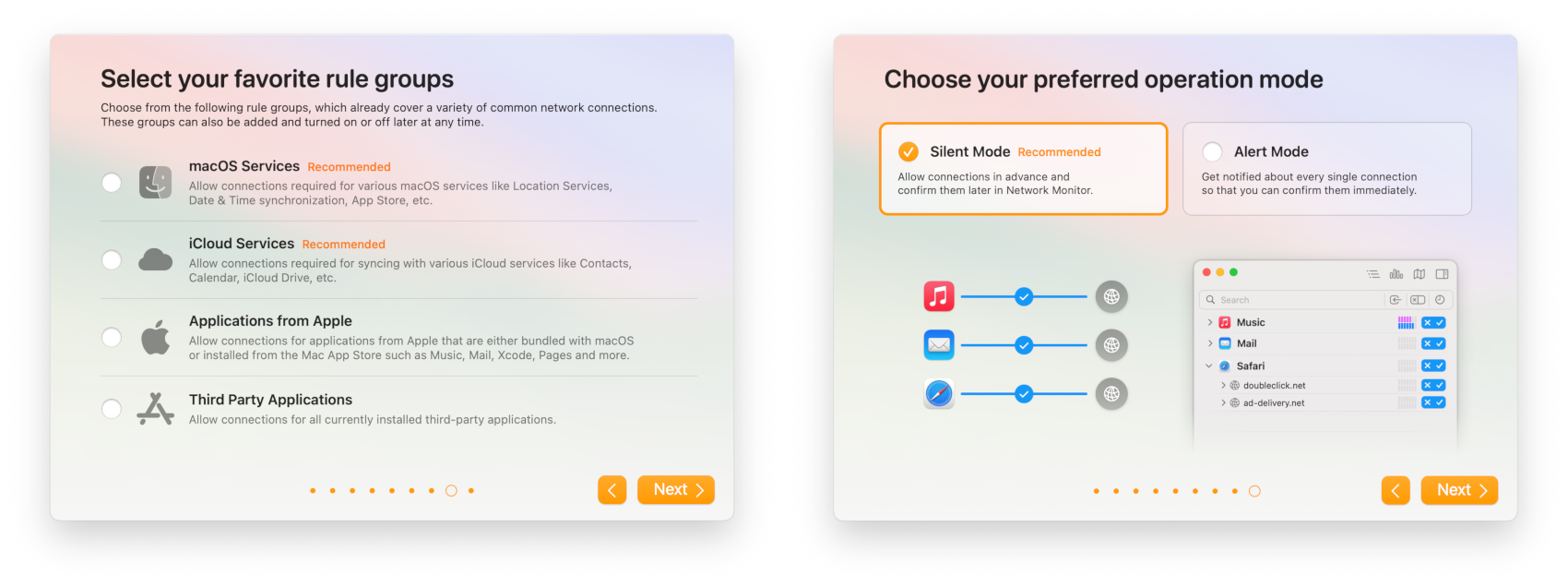
You can change your mind at any time later, so choose what you feel is appropriate for you.
Silent mode
Silent mode is based on the following idea: Instead of interrupting you with connection alerts over and over again, Little Snitch just allows all connections and records which app connected to which server. Later, when you take your time to decide about rules, you open Network Monitor to review connections that happened so far and decide what to allow and what to deny.
The advantage of this approach is that you can decide yourself when to dedicate time to Little Snitch and you can create an optimal rule set, tailored to your needs. The obvious disadvantage is that you do not enjoy the full protection immediately. But to be honest: You have probably been using your Mac for years without even knowing about these connections. Waiting at least one more day should not be much of an issue.
For more information on silent mode read the section explaining operation modes in more detail.
Rule Groups
Another option for limiting the amount of connection alerts is to create generous allow-rules at installation time.
Little Snitch offers pre-configured groups of allow-rules:
- macOS Services: Some people trust nobody but Apple, others trust everybody else but not Apple. If you trust Apple and don’t want to review any of the connections made by the operating system or connections to servers under Apple’s control, enable this rule group. It allows all system background processes to connect wherever they like and all apps to connect to Apple servers. These rules cover most of the connections made by a freshly installed macOS, but no apps.
- iCloud Services: Likewise, this rule group covers connections from any app into iCloud domains. This is a separate group because you may not be using iCloud even though you trust Apple.
- Applications from Apple: This rule group is created at the time you add it, based on currently installed apps. Little Snitch searches the standard locations for apps from Apple (recognized by their code signature) and creates rules allowing them any outgoing connection. This rule group makes sure that all Apple Apps can communicate without restriction. Note, however, that most of the apps found this way will never connect to a remote computer at all. Review the rules after several weeks and delete those which have a use count of zero.
- Third Party Applications: This rule group is also created at the time you add it by searching the standard locations for apps which are not from Apple. We do not recommend adding these rules because it defeats much of the purpose of Little Snitch. Some users still want to allow all pre-existing apps to prevent the flood of connection alerts after a new install. They argue that they trusted these apps before Little Snitch was installed and that they are only interested in new processes which they did not install intentionally.
For more information see the section explaining rule groups in more detail.
Blocklists
Blocklists are a quick way to add deny-rules for unwanted connections. They are immediately effective, even if you use silent mode and have not yet created any rules of your own.
Blocklists are maintained by volunteers and categorized by topic. There are blocklists specializing on ad servers, blocklists for servers tracking your behavior, for sites containing malware and so on. There are also blocklists of the type “one size fits all” which combine various topics.
In order to add blocklists, open Little Snitch and in the rules window click “Add Blocklists…”:
For more information see the section explaining blocklists in more detail.
Was this help page useful? Send feedback.
© 2016-2026 by Objective Development Software GmbH