Operation modes
When an app establishes a connection, it should usually be matched by an existing rule. The rule determines whether to allow or deny the connection. However, if no rule matches, the operation mode determines what to do.
Alert mode
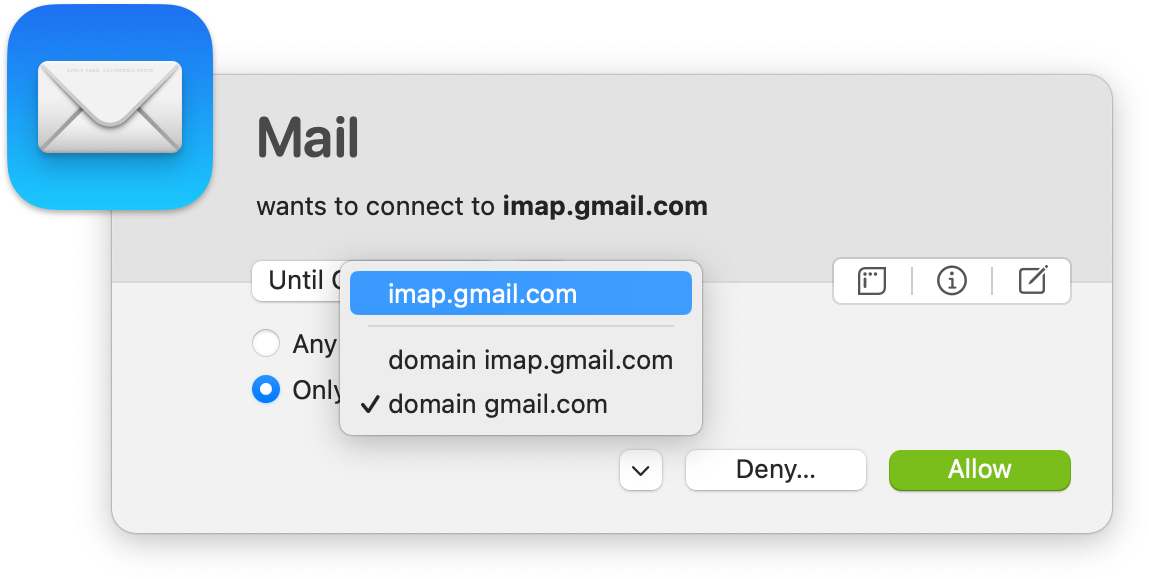
When no rule matches, Little Snitch presents a connection alert. By answering the alert, a new rule is created which covers this and future similar connections. In the factory configuration, the alert is pre-configured to create a rule for the entire destination domain, not just the particular host. You can fine-tune the rule directly in the alert and you can change the defaults in settings.
Silent mode
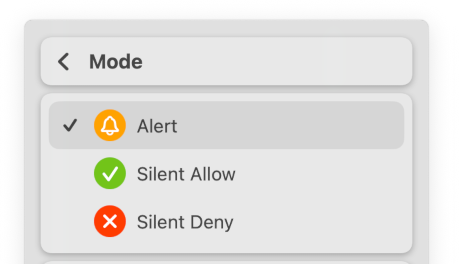
Silent mode comes in two flavors:
- Silent allow mode
- Silent deny mode
When no rule matches, the connection is silently allowed or denied, depending on the mode, but Network Monitor records that a rule should be made. We recommend silent allow mode to get started, but we do not recommend silent deny mode for most practical purposes. It is mostly there for completeness and may make sense on unattended servers with high security requirements. When we talk about silent mode without reference to allow or deny, we usually mean silent allow mode.
After running Little Snitch in silent mode for a while, the connection list in Network Monitor may look like this:
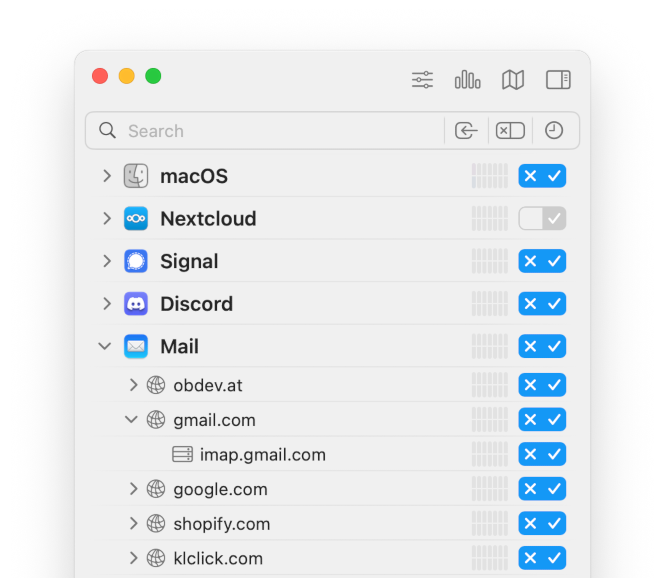
Blue rule management buttons indicate that your decision is pending. Let’s have a closer look at Apple’s Mail application. It connects to the domain obdev.at and gmail.com. obdev.at is there — you guess it — because our own mail server is in that domain. Click the right side of the blue button, the checkmark, to allow connections into this domain. For this example we also use Google mail (not because we recommend it in any way, just as an example). You can see that Mail connected to imap.gmail.com, Google’s server responsible for receiving e-mail via the IMAP protocol. Click the checkmark side of the button to allow it, otherwise you can’t receive mail via Gmail.
Note that Mail also establishes connections to other servers. Why is it contacting google.com? Why shopify.com? And what is klclick.com? Mail has received spam, mails from Google and newsletters from various companies which embed remote images. Mail has fetched these images from the respective servers. Most newsletters (and spams) use these images as a check whether your e-mail address is still valid. When you read the mail, Mail connects to the server to download the image. But each mail sent has a unique tracking number in every image URL so that the remote server can know which recipient is reading the mail.
Many people don’t like this type of tracking. To prevent it, just click the left side (with the “x”) of the rule management button right to Mail. Yes! Deny Mail any connection, because we made exceptions for all mail servers we need. The specific rules for those servers have precedence over the general deny for Mail. With these rules we make sure that Mail has no way to communicate any tracking information to outside servers.
You could argue that the Mail has a setting “Block All Remote Content” under “Privacy” which does exactly this. True, but did you try it? At least with macOS 14 up to 14.4.1, Mail still connects to servers referenced in newsletters. Our research seems to indicate that it just connects and does not download the content, but better be safe than sorry.
You get the concept: Wipe out all blue buttons by deciding which connections are allowed and which not. Decide on as high a level as appropriate to catch many connections with one click. Once you are done, switch to Alert Mode.
You will still have to handle a couple of connection alerts for connections which did not occur while you were in silent mode, but that’s OK. That’s Little Snitch in action.
Was this help page useful? Send feedback.
© 2016-2026 by Objective Development Software GmbH