Dieser Abschnitt ist leider noch nicht auf Deutsch verfügbar. Wir entschuldigen uns für die Unannehmlichkeiten.
Insights
This view helps you improve your rule set. It contains suggestions for rules you might want to add and hints to rules you might want to change or delete.
Suggestions
In some cases, Little Snitch automatically creates a rule for you, e.g. if you have selected Alert Mode but it was impossible to show an alert. These rules are often temporary rules. They are usually already expired when you open Little Snitch, but they contain valuable information about connections which were automatically allowed or denied and you might want to turn them into permanent rules. Little Snitch therefore preserves these expired rules as rule templates for you. They are available in the Suggestions section.
- Login — Temporary deny rules for connections which occurred before or during you logged in to your computer. Little Snitch denied these connections, short of a possibility to ask.
- Full Screen — Temporary deny rules which were created automatically while an application captured the entire screen (like games often do) and Little Snitch could not show a connection alert. You probably won’t see the suggestion before the rule has expired.
- Timeout — Temporary rules that were automatically created after an alert timeout. Alert timeouts are off by default and can be enabled in Settings > Alert > Confirm connection alert automatically.
- Expired — Expired temporary rules created by you. Instead of deleting these rules, Little Snitch lists them as suggestions because you may want to turn some of them into permanent rules.
Maintenance
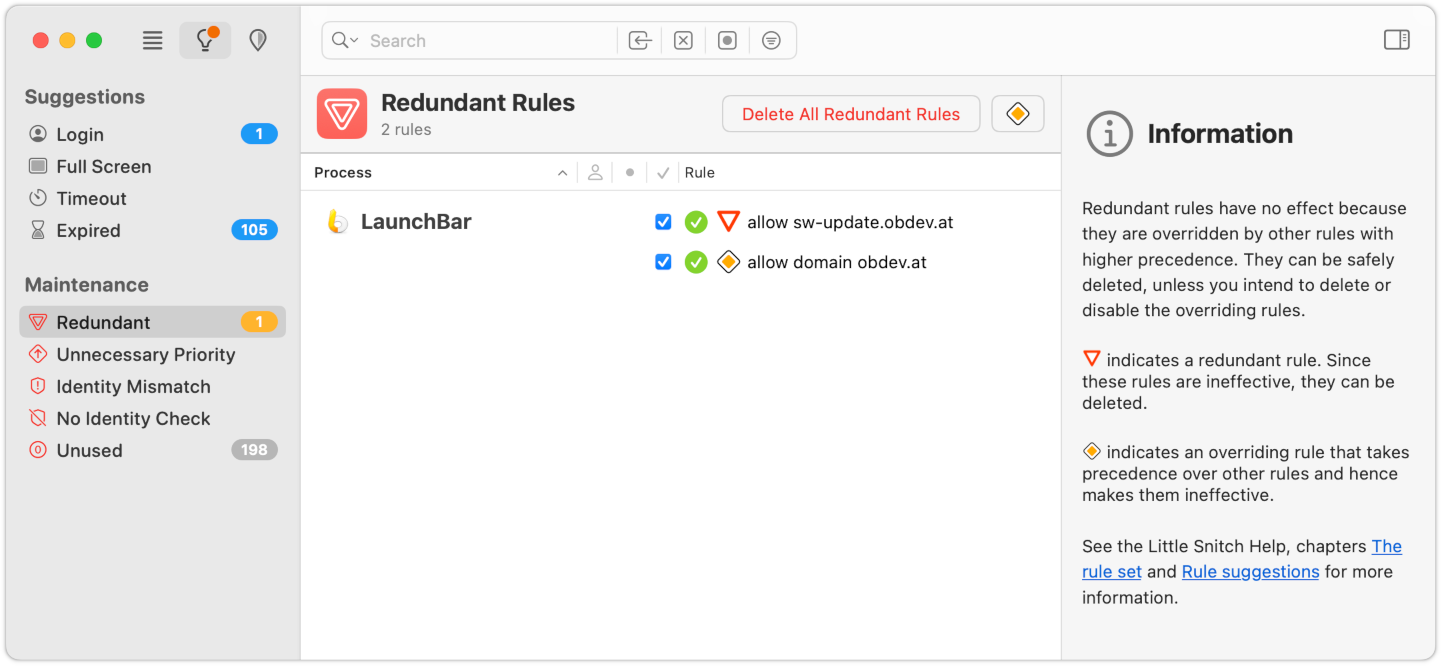
This section lists rules which require your attention because they are invalid, unnecessary or were not used for a long time.
- Redundant — Rules which are unnecessary because every connection they match is already matched by an other rule.
- Unnecessary Priority — Rules with increased priority, but the effect would be the same without priority.
- No Identity Check — Path based rules which do not check the process identity or Any Process rules which match untrusted processes. Consider enabling the check for these rules.
- Identity Mismatch — Rules that were created in an identity mismatch alert to prevent all network communication of a process in case of a failed process identity check.
- Unused — Rules which were not used to allow or deny connections for a long time. The top bar tells you how long that was. Note that there may be apps which are used only once a year or less frequently. Retain those rules, although they are listed as unused for a long time.
War dieser Eintrag hilfreich? Hinterlass uns Feedback.
© 2016-2026 Objective Development Software GmbH