Dieser Abschnitt ist leider noch nicht auf Deutsch verfügbar. Wir entschuldigen uns für die Unannehmlichkeiten.
Blocklists
Little Snitch helps you block unwanted connections. But researching each connection for every app is a lot of work. Wouldn’t it be great if somebody else could do that work for you? Blocklists are exactly that: Some people invest a lot of work into collecting names or IP addresses of servers with unwanted features. They publish these names or addresses, often in separate collections dedicated to specific topics such as tracking, ads, malware etc.
Little Snitch understands most of the blocklist formats found on the net, downloads the lists and integrates them into your rule set. It updates them from their sources on a regular basis, making sure they are up-to-date.
Blocklist Picker
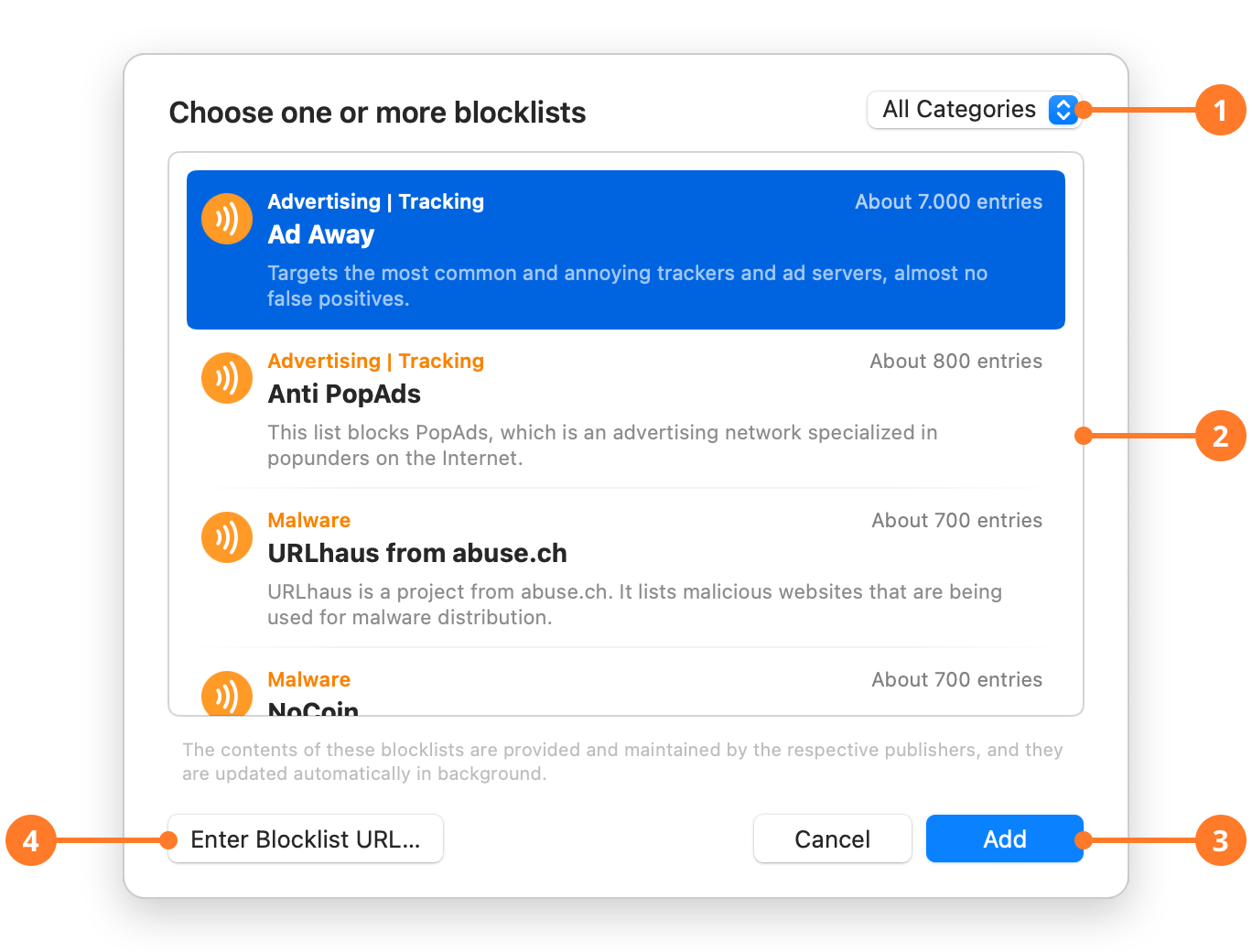
In order to make it easier for you to find suitable blocklists, Little Snitch offers a preconfigured set of blocklists for various topics. This set is downloaded from blocklists.obdev.at when you open the blocklist picker window by clicking “Add Blocklists…” in the left sidebar of the rules window (if no list has been added yet), or by clicking the “+” button right to the “Blocklists” section header:
| ITEM | DESCRIPTION |
|---|---|
| 1 | Click here to filter the displayed blocklists by category. Some blocklists specialize in tracking, others in malware, and still others in explicit content. Some blocklists even combine several topics. |
| 2 | Lists all blocklists for the selected category. The orange text above the title tells you in what categories the list specializes in. Below the title, there is a short description, and to the right of each entry is an estimate of the number of domains or servers included in the list. |
| 3 | Select one or more blocklists you want to add and click “Add” to use them. |
| 4 | If your favorite blocklist is not contained in our list, you can add it manually by providing its URL. |
The blocklists offered here are maintained by third parties and Objective Development has no affiliation with them. Visit the publisher’s web site to get more information. Blocklists have been selected by the following criteria:
- The list is still maintained, last update is reasonably new.
- Updates are made frequently.
- The list exists for at least a year.
- The number of entries is not abundant. This indicates that the maintainer actively removes outdated entries.
- There appears to be a community supporting and using the list.
- The list is relevant for macOS (not just Windows malware).
- We try to limit the number of lists in each category.
Choosing a set of blocklists
Although we do not recommend particular lists, we can give you a guideline how to choose what is suitable for you.
- More is not better. Each list contains “false positives”. A false positive is a site blocked by the blocklist which you don’t want to block. An example: Peter Lowe’s list blocks
t.co, a shortcut URL for X (formerly known as Twitter). There are good reasons to include it because it meets the criteria of the list’s topic, but if you use Twitter, you rather want to disable this entry. - Decide on the categories you want to block. There is no need to block gambling or explicit content if you don’t need to protect yourself or family members from that content. There is no sense in blocking ads if you (or a family member) usually follow Google’s recommendations for shopping.
- Look at the blocklists in the given categories. Decide for one or at most two of them, based on whatever information is important for you.
- You may look at blocklist usage statistics after a while to see how effective each blocklist is. But be careful: If a list blocking malware will hopefully have a use count of zero! If it protects you from a virus infection only once in your entire lifetime, it may be worth it. You don’t want to see malware lists being used, but tracker and ad lists will have noticeable counts.
Supported Formats
Little Snitch supports the following formats:
- hosts: If the downloaded file appears to be in
/etc/hostsformat, the list is treated as blocklist of computer names. - domains: If Little Snitch can identify many computer names separated by any type of separator (newline, comma, etc), it treats them as blocklist of domain names. The domains themselves and all computer names in the domains are blocked.
- IP addresses: If the list consists of IP address ranges, either in the format
1.0.0.0-1.255.255.255(range representation) or in the format1.0.0.0/8(CIDR representation), it is interpreted as IP address blocklist. - .lsrules: This format has been made to archive arbitrary groups of rules. If it “looks like a blocklist”, it is shown in the Blocklists section. A rule group looks like a blocklist if it contains only entries which deny hosts, domains or IP addresses for any process. If a blocklist is available in multiple formats, we recommend that you avoid
.lsrulesbecause the other formats are more compact.
War dieser Eintrag hilfreich? Hinterlass uns Feedback.
© 2016-2026 Objective Development Software GmbH