Dieser Abschnitt ist leider noch nicht auf Deutsch verfügbar. Wir entschuldigen uns für die Unannehmlichkeiten.
Connection alert
When Little Snitch encounters a connection attempt that is not yet covered by a rule and Alert Mode is active, it shows a connection alert, asking you whether to allow or deny the connection. Answering the alert creates a rule which matches the connection. The next time the connection is attempted, it is covered by the rule you just created and the rule determines whether to allow or deny it.
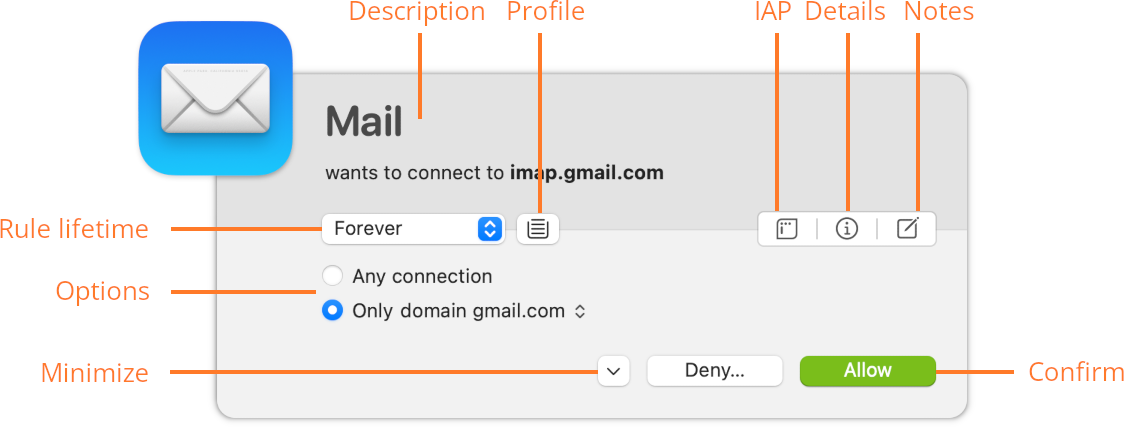
- Description — Name of the connecting process and remote server1. If an app uses a helper process to establish the connection, the name of this helper is shown next to the app name (e.g. “LaunchBar via ssh”). Depending on your detail level setting in Alert Settings, port number and connection protocol are shown as well.
- Rule lifetime — Rules can be automatically deleted at a later date. Choose “forever” or the event for which the rule should be deleted.
- Profile — Click to choose whether the rule should be created in the current profile or effective in all profiles. By default, rules are created in the current profile. This can be changed in SettingsAlert Settings.
- Options — These options determine how specific the remote host is matched2. The set of options depends on the detail level setting in Alert Settings, but the full set is always available when the Details section is open. Click the domain name for a menu to choose between domain and host rules.
- Confirm — Decide whether to create an Allow- or Deny-rule.
- IAP — Internet Access Policy, if available for the process. Click this button to get more information about the purpose of the connection.
- Details — Click this button to reveal all technical details.
- Notes — Rules can be annotated. If you want to add a note, e.g. why or when the rule was created, click this button.
- Minimize — If you don’t want to handle the alert immediately, you can minimize it.
-
If no name for the remote host can be obtained or if it is not unique, the host’s Internet address is shown. If the name is not unique, but all potential names for the host are in the same domain, the common domain is also mentioned. ↩
-
In fact, the remote end of the connection can also be the Berkeley Packet Filter. This is a low level operating system service which can be used to eavesdrop on all network communication or inject and receive any type of network data. Strictly speaking, it is not a remote host but a service which can be used to contact remote hosts. ↩
War dieser Eintrag hilfreich? Hinterlass uns Feedback.
© 2016-2026 Objective Development Software GmbH