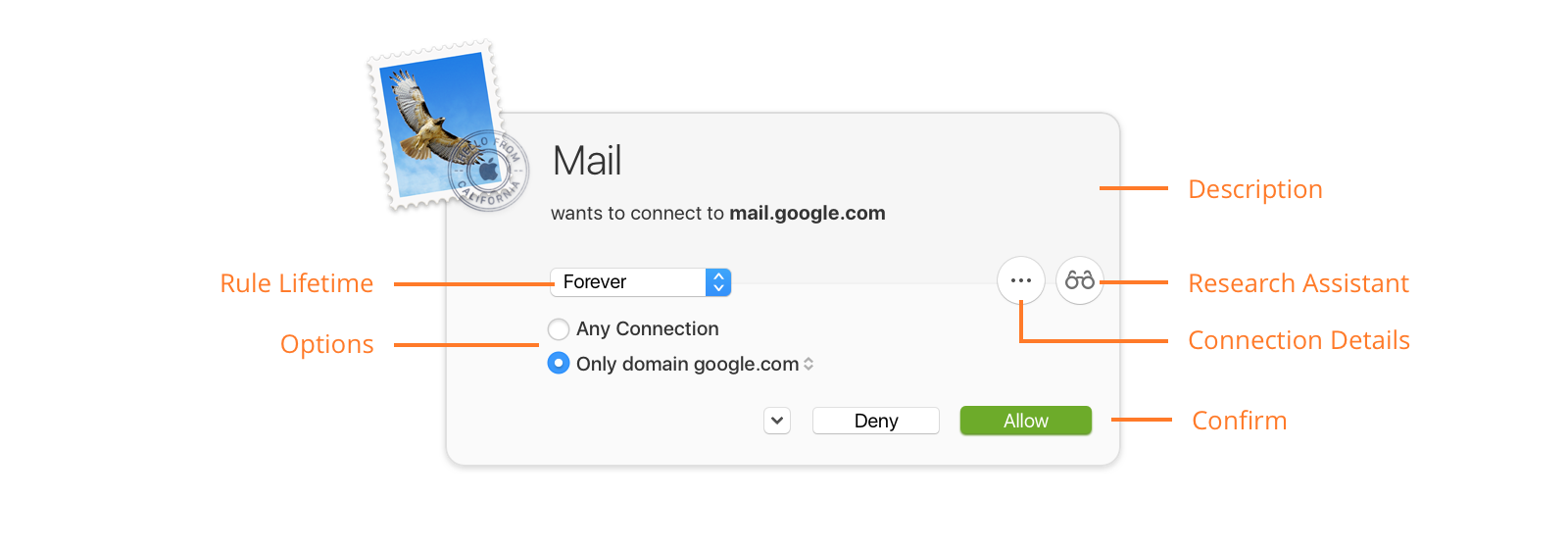
Connection alert
When Little Snitch encounters a connection attempt that is not yet covered by a rule and Alert Mode is active, it shows a connection alert, asking you whether to allow or deny the connection. You usually do this by creating a rule which matches the connection and, depending on your choices, other similar connections. The next time the connection is attempted, it is covered by the rule you just created and the rule determines whether to allow or deny it.
The connection is stalled until the alert is answered or a rule matching the connection is created. This means that the process trying to connect is paused and may not respond to your input, unless it performs the connection in background.
Description section of alert
The description provides a brief summary of the connection attempt, including the names of involved processes and servers. If an application utilizes a helper tool to establish the connection, the name of this tool is shown next to the application name (e.g. “LaunchBar via ssh”).
If no name for the remote host can be obtained or if it is not unique, the host’s Internet address is shown. If the name is not unique, but all potential names for the host are in the same domain, the common domain is also mentioned.
Learn more about how Little Snitch determines the server name…
Depending on your detail level setting in Alert Preferences, port number and connection protocol are shown as well.
Getting more information
- Research Assistant — Click this button to get more information about the purpose of the connection.
Learn more about Research Assistant… - Connection Details — Click this button to reveal all technical details in both sections. The Description Section shows process ID, process owner, Internet address and more, while the Rule Creation Section expands to all available options.
Rule creation section of alert
You confirm the connection alert by creating a rule matching the connection. This section lets you choose the parameters of the rule. The alert lets you only create rules which match at least the connection currently displayed, but the rule may match much more.
Rule creation options
- Rule Lifetime — The rule created can be valid forever or temporarily (until logout or restart, until the process terminates or for a period of time). The option Once affects only one data packet and no rule is created.
- Options — These options determine how specific the remote host is matched1. The set of options depends on the detail level setting in Alert Preferences. The domain or host name has a pop-up menu where you can choose whether to create a rule matching an entire domain or the specific host only. In order to see all options, click the Connection Details button.
- Profile Option — If a profile is active, you can decide whether to create the rule in the current profile or make it effective in all profiles. If the button is highlighted, the rule is created in the current profile.
- Confirm — Decide whether to create an allow or deny rule.
Touch Bar controls
If your Mac has a Touch Bar, you can confirm the connection alert by tapping the Allow or Deny button. These behave just like the respective buttons in the connection alert itself and use all the other settings for rule lifetime, remote host and profile as you would expect:

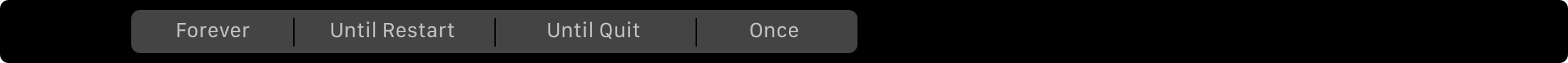
But if you tap and hold either the Allow or the Deny button, you can select the rule lifetime by sliding to the desired segment on the Touch Bar:
-
In fact, the remote end of the connection can also be the Berkeley Packet Filter. This is a low level operating system service which can be used to eavesdrop all network communication or inject and receive any type of network data. Strictly speaking, it is not a remote host but a service which can be used to contact remote hosts. ↩
Was this help page useful? Send feedback.
© 2016-2026 by Objective Development Software GmbH