Inspect and analyze rules
If you want to know why a connection was allowed or denied, it’s probably easiest to start analyzing the issue in Network Monitor using the Show Corresponding Rule context menu option.
See the precedence of rules
Little Snitch determines automatically which rule has precedence over other rules. The general concept is that more specific rules override more general rules.
It is not always easy to determine precedence from rule properties alone. Little Snitch Configuration can help: To sort rules by precedence, click the Rule header of the list or choose View > Sort By > Precedence from the main menu. Rules further at the top of the list now have precedence over rules that are below them:
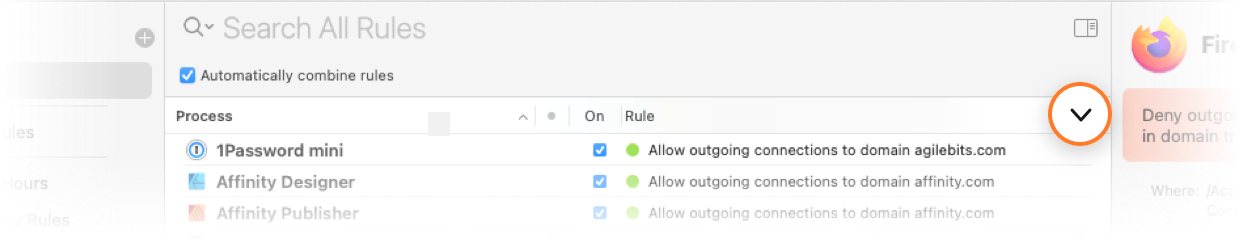
Note that when sorting by precedence, rules for a particular process may not necessarily be all next to each other. They may be spread across the list, separated by Any Process rules and rules for other processes.
If you are wondering why a particular connection was allowed or denied, right-click the process attempting the connection in the rule list and choose Focus on Rules Affecting… in the context menu. This sets the process name as the search term, sets the search scope to the exact match of the process and sorts rules by precedence. The result is a list where you see only rules affecting the process with decreasing precedence.
You can also right-click the connection in Little Snitch Network Monitor and choose Show Corresponding Rule to see the rule responsible for allowing or denying the connection, but you will not be offered the information as to why exactly this rule had the highest precedence.
Sorting rules
Besides sorting rules by precedence, you can also sort by process name (click the Process table header) or by rule creation date (click the • table header). Additionally, sort options are also available in the main menu under View > Sort By.
Check for redundant rules
Imagine the following situation: Little Snitch shows a connection alert for a new application and asks whether it may connect to domain vendor.com. You allow it. After a while, it asks for domain vendor-cloud.com. You allow it as well. Then it asks for domain vendor-download.com. Now you decide to allow the application Any Connection.
With this last rule in effect, the previous two rules have become unnecessary (redundant). You can delete them and nothing will change in the behavior of Little Snitch.
With Little Snitch Configuration, it’s easy to find these unnecessary rules:
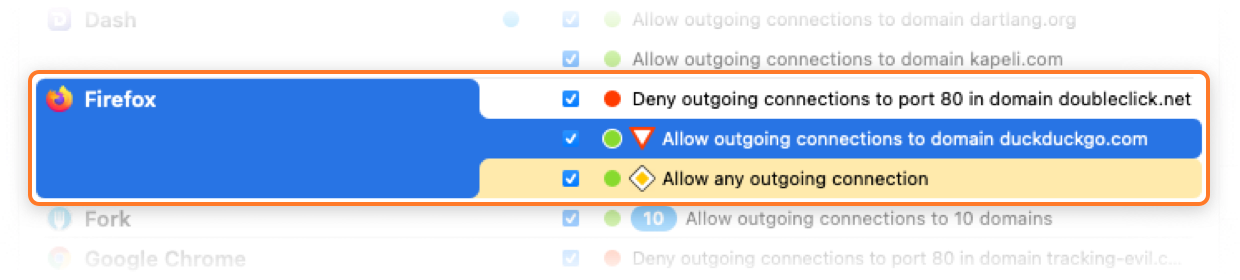
Redundant rules are marked with the symbol ![]() . When you select such a rule, Little Snitch Configuration explains why it is redundant. The rule that covers it has a yellow highlight. Rules making other rules redundant (covering them) are marked with the symbol
. When you select such a rule, Little Snitch Configuration explains why it is redundant. The rule that covers it has a yellow highlight. Rules making other rules redundant (covering them) are marked with the symbol ![]() .
.
Little Snitch does not automatically delete redundant rules because you may decide to delete the covering rule later or the covering rule may have been created by mistake.
Unnecessary priority
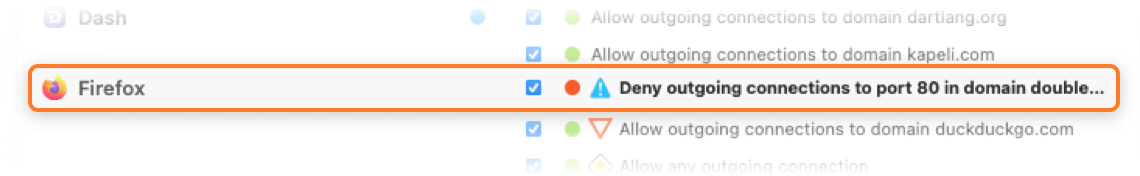
Rules can be set to have increased priority, which may be useful in profiles to override the default behavior. Similar to redundant rules, this priority may be unnecessary. If the rule’s precedence in relation to all other rules is the same with or without the priority setting, the priority can be lowered.
Little Snitch Configuration marks these rules with the symbol ![]() :
:
Was this help page useful? Send feedback.
© 2016-2026 by Objective Development Software GmbH